If you are unfamiliar with the concept of multihoming in the context of Log Analytics Workspaces you can read the introduction article here.
TLDR: At the end of the introduction, I concluded the most likely scenario you would implement in an AVD environment with both operational and security monitoring requirements would be a multihomed setup.
A recap below if you have skipped to the introduction article how to.
In a multihoming scenario:
- The AVD operational data is forwarded from the AVD service to a LAW allocated for both operational and security data (Point 1 below)
- The AVD operational data is consumed from AVD Insights (Point 2 below)
- The LAW sits atop Azure Sentinel (or similar 3rd party product) where the AVD security data can be consumed by your security team. (Point 3 below)

This article will concentrate on the configuration of the Azure Monitoring Agent (AMA) and associated Data Collection Rules (DCRs) (point 3) and while you can deploy the script in a different build/deployment tool it assumes you are using Scripted Actions in Nerdio.
Some configuration is outside the scope of this article and wont be covered:
- If you are already using Nerdio Manager for Enterprise operational data collection (points 1 and 2) will be configured for you out of the box. If you are not using Nerdio the manual setup for AVD monitoring is well documented by Microsoft here.
- Configuring Azure Sentinel (point 4) to consume the LAW data is also outside the scope of this article and is documented by Microsoft here.
Before starting if you need a broader understanding on how the AMA and DCRs can be configured and deployed check out these articles:
- Markus Lintuala’s article provides a nice overview on AMAs and DCRs in general.
- Johan Vanneuvill’s practical walkthrough article on setting up AVD monitoring using AMA.
- Robbe Van den Daele’s in-depth overview article of DCRs and Transformations.
Important Warning: The scripts provided in this blog are freely and gladly shared. They are intended solely for testing and educational purposes. They are not recommended for use in production environments unless thoroughly tested. Please be aware that using these scripts is at your own risk.
Implementation
For the purposes of this demo, I have created a dummy LAW called Security-Test.

Note: With AMA configuration the rules have moved away from direct configuration of the LAW into Data Collection Rules. Also the AMA uses managed identity so no need to manage the workspace ID and Keys.
To complete the configuration using the AMA, you will need the following details from your environment:
- Subscription ID (note when using Nerdio Scripted actions this is provided as a default variable)
- Resource Group of your designated security Log Analytics Workspace
- Log Analytics Workspace Name
- Workspace ID (available in the Agents tab of your designated LAW)
- Azure Region of the LAW (this will typically be the same region as your AVD compute and the region you will place your Data Collection Rules in)
Once you have gathered this information download the AMA script here, open in the editor of your choice and make the following changes:
Optional Line 86: You will need to explicitly add your Subscription ID if using script outside the Nerdio context.

Required Line 89-92: The Target LAW variables can be obtained from Azure Portal or your LAW Administrator if outside your permissions scope.

Required Line 96-97: Data collection rule Name and Description can be set to comply with your environment naming conventions

Optional Line 101: The Data Collection Rule Resource Group will leverage Nerdio variable $AzureResourceGroupName and will mirror the target Resource Group the VM is being created in. You will need to explicitly set this if using script outside the Nerdio context. Additionally you may want to place your Data Collection rule in a different Resource Group.

The script to deploy the AMA and the associated Data Collection Rules is a little more involved than its MMA counterpart for several reasons:
I am utilizing the AZDataCollectionRule PowerShell commands provided in the Az.Monitor module. The command requires that you pass your Data Collection Rules in JSON format. To achieve this in the context of an Azure Run Book/Nerdio Scripted Action I define the Data Collection Rules as a Hashtable before converting to a JSON object in lines 135-164.

Note: I have defined my rules for the collection of Security events as an XPathQuery. This IBM support article gives a nice concise explanation on how to use Microsoft Event Viewer to create an XPATH Query if you need to expand on this ruleset.
The commands to check for the existence of the Data Collection Rule and create one if it does not exist can be found in lines 181-200

Note: You might want to run the Data Collection Rule and definition creation sections in a standalone script but as I would like to run these activities in the context of a VM build sequence I have wrapped it in detection logic to prevent it running when it is not necessary.
In the case of the AMA script, I have added a section to install the extension in lines 202-216.

Note: It is a valid strategy to deploy your AMA via Azure policy if you have a wider roll out program in your tenant but in the context of AVD I personally prefer to descope wider Azure policy for the AMA from my AVD environment and manage deployment as part of my build pipeline/sequence.
I have also added a section to the script to include Data Collection Rule association for the target VM in lines 231-247

Note: It is also a valid (arguably better) strategy to manage DCRs and associations with Azure Policy but I have included it in a self-contained script that can be scoped to a single VM build.
For my demo environment I have updated the script with the following variables:
$LAWResourceGroup = “RG-Nerdio” (For simplicity and the demo’s sake I am keeping my security LAW with my other Nerdio objects.)
$LAWName = “Security-Test” (LAW name created as per initial steps above)
$LAWId = “xxxxxxxxxxxxxxxxxxxxxxx” (Retrieved from the Agents tab of the created security LAW)
$LAWRegion = “North Europe” (The Azure region I am using for demo)
$DCRName = “AVD-Security” (The Data Collection Rule Name)
$DCRDescription = “Data Collection Rule to capture Security Audit event logs in the AVD environment” (The Data Collection Rule description)
Now you have updated the script with the required variables open the Nerdio Manager for Enterprise portal -> Scripted Actions -> Azure runbooks

Note: In the case of deploying the AMA and Data Collection Rules the script needs to run in the context of the Azure environment rather than on the VM itself as would be the case when deploying and configuring the MMA. This is why we choose the Azure runbooks rather than Windows scripts.
A bottom right of scripted actions, click on Add Scripted action.

Enter the following details below:
Name: Add Log Analytics Workspace (AMA) <Insert LAW name here>
Description: This script is used to configure a Log Analytics workspace in Azure by setting up a Data Collection Rule (DCR), associating it with a Virtual Machine (VM), and installing the Azure Monitor Agent (AMA) extension on the VM to facilitate data collection and logging.
Tags: The tags are optional but as this is a script made up of PowerShell commands are all Microsoft based and for MS based technology you can tag it as Microsoft
Script Execution Mode: This can remain on Combined it has no requirements to be run separately and it won’t trigger a reboot.
Script: Copy and paste your modified script into this section
Click Save and close.

You will see your script in the Azure runbooks section.

Testing
Browse to Workspaces -> Dynamic host pools and choose the host pool where your test VM lives.

To the right of your test VM name, details and status click the drop down beside the Power off button and choose Run script.
Search for your Add Log Analytics Workspace (AMA) <LAW name> script, choose it from the drop down and click Run Now

Verification
You can track the status of the script in the Host Pool Tasks pane.
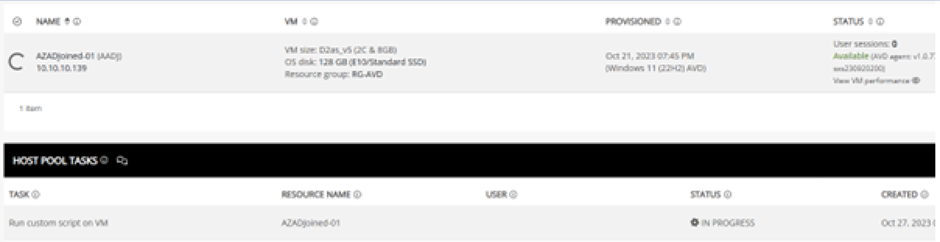
While the task is running or after it is completed you can click on Details on the right of the task entry.

This allows you to see the details of the Scripted Action execution. We can see below the script has completed without error

In the step directly below this step, you will be able to expand the output from the Azure runbook scripted action and check the output logging by clicking on > Show

You will be able to see the output logged by the script during execution. A successful run will look something like the below:

You can also verify the completion of the script in the Azure Portal by browsing to Data collection rules -> AVD-Security (or the name you gave your designated Data Collection Rule) -> Data sources

And the VM association at Data collection rules -> AVD-Security -> Resources

Next browse to Log Analytics workspaces -> Security-Test (or the name you gave your designated security LAW). Open a query and type Event in the query field and click Run, you should see the security audit logs coming from your VM.

Deployment
Now you want to take the Scripted Action and add it to your AVD build sequence. In Nerdio you can browse to your chosen hostpool at Workspaces -> Dynamic host pools
Then click on the drop-down button beside Manage Hosts to the right of the management pane and choose Properties.

On the Properties page click on VM Deployment

You will want the additional LAW to be added each time a new VM is provisioned in your hostpool. For that reason, choose Run Scripted actions when host vm is CREATED.

Search for Scripted Action by name, add it from the drop-down menu and click Save and close:

You will see the update configuration task complete in the HOST POOL TASKS pane.

To test this click on Drop Down menu beside Manage Hosts -> Hosts -> Add new

Choose the settings for a new VM particular to you:
Host Count: 1
Note: As this is just a test of the scripted action in a build sequence one VM is enough.
Host Name: AZADJoined-02 | Exact
Note: This will build the VM with the exact entry specified (no additional prefix or suffix)
DESKTOP IMAGE: Windows 11 (22H2) Enterprise – Gen2 (single-session)
Note: This is a single session test Hostpool so choosing latest Windows image, choose what is relevant to you.
VM SIZE: D2as_v5
OS DISK: 128GB (E10 Standard)
RESOURCE GROUP: RG-AVD
Note: Choose what is relevant to your hostpool.
When you are satisfied with selections click on Run Now.

As before you can see the Add host in the HOST POOL TASKS pane. Click on Details on the right of the Add host task entry.

If you are using Nerdio to configure your Primary LAW for AVD Insights, you will see it competing in the build sequence log below.

Further down in the build sequence log you will see the Add Log Analytics Workspace (AMA) AVD-Security running AFTER the VM has registered with the AVD service.

And verify your most recent VM has been associated with the DCR at build time in Azure portal by browsing to Data collection rules -> AVD-Security -> Resources

Finally browse to Log Analytics workspaces -> Security-Test (or the name you gave your designated security LAW). Open a query type Event | where Computer == “<VMname>”in the query field and click Run, you should see the security audit logs coming from the VM.

